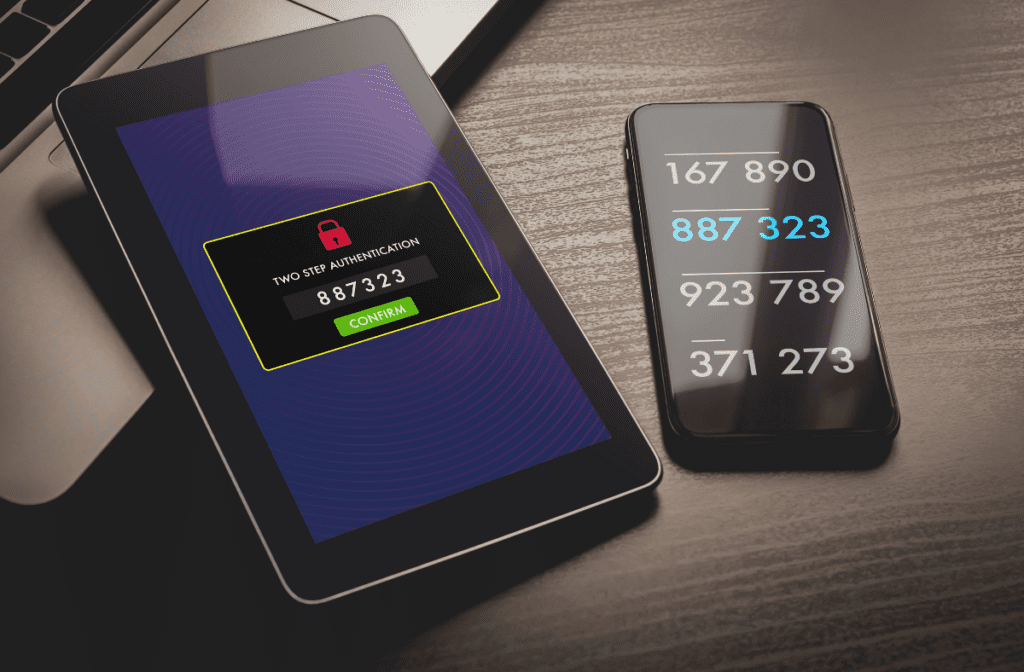
Two-factor authentication (2FA) is a security mechanism that requires the user to provide two different forms of identity verification when accessing digital systems or services. These two factors usually include something the user knows (such as a password) and something the user has (such as a mobile phone or token). The combination of these two factors increases access security and minimizes the risk of unauthorized access.
In a digital environment where rapid technological advances are taking place, security is a key factor in protecting sensitive data and information. Two-factor authentication provides an effective means of preventing unauthorized access and protecting against potential security threats such as identity theft, phishing, and account attacks. It is essential for users and organizations that value the security of their digital activities and accounts and Internet security.
How Does Two Factor Authentication Work?
Two-factor authentication (2FA) is a security mechanism that requires two different ways to verify a user's identity. In this way, the level of protection of digital accounts and information is increased. The basic concept consists in the combination of several authentication factors that the user must pass successfully in order to gain access to the system or service.
Two-factor authentication combines several categories of authentication factors. The first factor is usually something the user knows, such as a password. The second factor is something the user has, such as a physical device or biometrics. The combination of these two factors increases security by requiring additional verification even if one factor is compromised.
Forms of two-factor authentication
Code sent to mobile phone:
- One of the most common methods of the second verification factor is to send a one-time code to the user's mobile phone. This code can be obtained via SMS, mobile apps or email.
Hardware tokens:
- Hardware tokens are physical devices that generate or display one-time codes. The user can carry the device with him or use it only during specific logins. This form provides an additional layer of protection.
Biometric data:
- Biometric two-factor authentication uses physical characteristics of the user, such as fingerprints, facial recognition or eye scanning. This data is unique for each user and provides a high level of security.
Applications for generating codes:
- Users can use mobile applications that generate one-time codes, for example using the TOTP (Time-Based One-Time Password) algorithm. These codes are automatically renewed after a certain time, increasing security.
Reasons for Using Two-Factor Authentication
Two-factor authentication (2FA) is becoming an essential tool in the fight against security threats in the digital environment. Its implementation brings several key advantages:
Increased Security
Protection against password theft:
- One of the main benefits of 2FA is the elimination of the vulnerability associated with using only passwords. Passwords can be easily compromised through phishing, social engineering, or data breaches. 2FA ensures that even if an attacker obtains the password, they cannot gain access without a second authentication factor.
Resistance to account attacks:
- Account attacks are a common occurrence in the digital world. 2FA increases resistance to these attacks because even if an attacker obtains the password, they will not be able to gain access without the second factor.
Prevention of Phishing and Malware
Implementing 2FA reduces the risk of successful phishing, where an attacker tricks users into providing sensitive information. The combination of something the user knows (password) and something the user has (for example, a code sent to a mobile phone) complicates the attacker's task.
Additional Advantage When Losing Your Password:
2FA provides an additional layer of protection when a password is lost, either due to forgetting or theft. An attacker would need not only the password, but also access to the second factor, which complicates unauthorized access and increases the security of digital accounts.
Given the ever-increasing risks associated with cyber threats, two-factor authentication is a key tool for protecting user accounts and sensitive information. It's an investment in security that ensures digital identities are effectively protected against modern security challenges.
Risks and Limitations of Two-Factor Authentication
Two-factor authentication (2FA) has many benefits, but it is not flawless, and there are some challenges and limitations to consider.
Possible Security Deficiencies
When implementing 2FA, there are potential risks that can compromise its effectiveness. For example, if a second authentication factor such as a mobile phone or hardware token is lost, the user may have problems accessing their account. Furthermore, some forms of 2FA, such as SMS codes, may be more vulnerable to attack if an attacker manages to gain access to a user's mobile number.
User Convenience vs. Security:
Finding a balance between user convenience and security when using 2FA can sometimes be a challenge. Some methods may be considered impractical or unnecessarily complicated by users, which may lead to reluctance to use this security layer. Proper implementation and user education on the importance of 2FA can help overcome this challenge.
Technological Challenges and Compatibility:
2FA may encounter technological and compatibility challenges when integrating with different systems and services. Not all digital platforms support the same forms of 2FA, and this can cause problems if a user wants to use this layer of security across different applications and systems. There may also be a question of compatibility with different types of hardware tokens or biometric systems.
Conclusion
In conclusion, it can be concluded that two-factor authentication (2FA) represents an important security measure in the digital world. Despite some challenges, such as possible security flaws or limitations in user convenience, 2FA is essential to protect against cyber threats.